What to Prioritize for a Secure Password Strategy
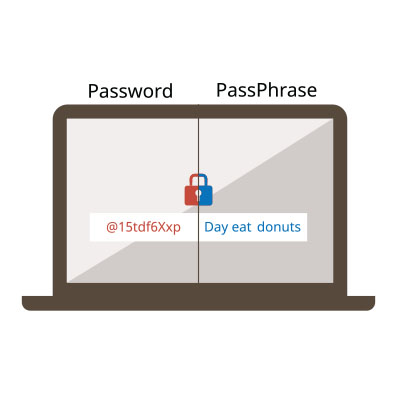
Securing your accounts against unauthorized access begins with the implementation of a strong password. It’s crucial to recognize that not all passwords offer the same level of protection. Here are five essential guidelines to ensure the security of your accounts.
Network Drives: What All Those Letters Mean for Data Management
You often hear about “drives” when working with technology, but there are many different types that a computer might use in your business’s day-to-day operations. Today, we want to explain what some of these drives do and why you should know where they are and what they stand for.
Three of the Biggest Security Solutions You Might Not Be Using

Your typical IT professional might suggest some common methods of network security like implementing better preventative measures, like firewalls and antivirus. However, there is more that goes into network security—far more. If you’re not careful, you could accidentally miss some of these three security solutions and expose your business to potential threats. But we’re not […]
