Three Ways to Use the Cloud to Dodge Hardware Costs

With the price of hardware at risk of skyrocketing, it’s no wonder that many businesses are looking to virtualize as much of their operations as they can. This is where the cloud comes in; you can virtualize just about any solution, including some that you might not have considered in the past. Let’s explore how […]
Remote Work Isn’t All Sunshine and Roses

Remote work isn’t a new strategy, but ever since the COVID-19 pandemic shut down in-office activities for all types of businesses, the amount of remote workers has grown regularly. In 2024, nearly 22 million workers would be considered fully remote, with over twice that amount working a hybrid schedule where they are remote at least […]
Four of the Best Practices to Secure Password-Protected Accounts

Passwords are the most important security tool used to secure digital assets. They are critical for small businesses, as weak or mishandled credentials can lead to serious security problems. Everyone must understand and follow the best practices for creating and managing passwords. This month, we will go through a few of them.
Why Your Business Needs Server Management Support (and How You Can Get It)

Do you ever feel at home in your business’ server room? That is, assuming you have a server room, and it’s more than just a stuffy closet in an isolated part of your office. If you’re not confident that you can provide your servers with the management, maintenance, and monitoring they need, we recommend you […]
Five Simple Tips to Get Your Smartphone to Last Longer

Your smartphone is probably one of the most important tools in your daily life. It helps you stay connected, entertained, and organized. But let’s be real—smartphones aren’t cheap, and replacing one every couple of years can hurt your wallet. The good news? With a little care, you can make your phone last longer. Here are […]
Tip of the Week: Simple Privacy Steps on Android
Your Android device offers a lot of capabilities in its little frame, with many people relying on theirs to keep their lives organized and generally handled. Many businesses even rely on Android mobile devices. This should only reinforce how critical privacy and security are. In light of this, we’ve shared a few simple tips anyone […]
How Outsourced IT Services Defy the Project Management Triangle
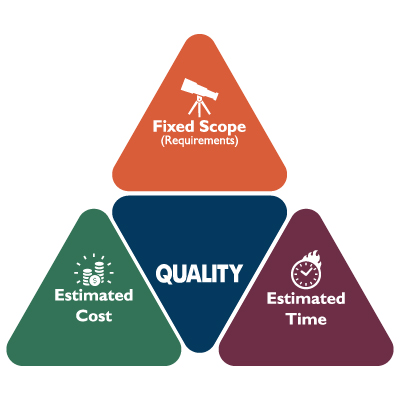
There is a concept known as the iron triangle that provides a simple framework for project management by outlining the balance between your costs, your available time, and the desired quality of your outcome. Traditionally, the iron triangle helps illustrate how these factors impact each other. Instead, we wanted to take advantage of the principles […]
Still Need a Resolution for New Year’s? Consider These Career and IT-Based Ones

Happy New Year! This time is usually dedicated to making plans and commitments to improve oneself over the coming months in the interest of the future. In the spirit of the holiday, let’s talk about how the right resolutions can help your career or your business’ use of technology.
Why Data Privacy is Important and How You Can Make It a Priority

Since so much of the world is now online, businesses and organizations interact with people online now more than ever. This means they also collect people’s information, a practice they do for various reasons. Individuals need to consider their own data privacy and how it might be affected by business practices.
AI IT Support Can Free Up Technicians… At a Cost

The big thing in business computing is AI, or artificial intelligence, and businesses are implementing it to solve a lot of repetitive problems that free up their employees to serve other roles. One such area is for IT support. But is it worth it to chat with a robot when something as important as IT […]
