Virtualization Translates to More Savings, Efficiency, and Security

How often does your business find that it’s struggling with new technology implementation, either on the software side of the house or on the hardware side? Have you considered that the cloud provides powerful solutions to your business’ woes in the form of virtualization? With the right resources at your disposal, you can use virtualization […]
All SMBs Need a Reliable VPN

Remote employees are in a conundrum when it comes to data security. While you might be able to protect data stored locally on your company’s in-house network, securing data in use by employees while out of the office is another matter entirely. How can you guarantee that your business is protecting its data and other […]
Three Ways You Benefit from Encrypting Your Email

Encryption stands as a formidable shield for businesses, fortifying their security architecture. While often discussed in VPN contexts, its significance in securing email solutions cannot be overstated. Why is email encryption indispensable for businesses of all sizes? Let’s explore.
Cloud Waste and What You Can Do About It

The cloud has become a go-to resource when businesses are trying to find and consistently depend on digital tools that otherwise would be out of their price range. One cloud issue that isn’t often mentioned in the course of choosing computing resources is cloud waste. Cloud waste refers to the inefficient or unnecessary consumption of […]
Network Drives: What All Those Letters Mean for Data Management
You often hear about “drives” when working with technology, but there are many different types that a computer might use in your business’s day-to-day operations. Today, we want to explain what some of these drives do and why you should know where they are and what they stand for.
What to Prioritize for a Secure Password Strategy
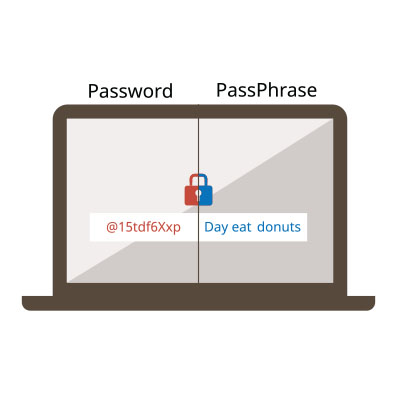
Securing your accounts against unauthorized access begins with the implementation of a strong password. It’s crucial to recognize that not all passwords offer the same level of protection. Here are five essential guidelines to ensure the security of your accounts.
Is Your Organization Prepared to Invest What is Needed into Cybersecurity?

Safeguarding your business’ infrastructure from various threats is a well-known imperative. In discussions about network security, the term “endpoint” frequently arises. Exploring the significance of securing all endpoints is the focus of today’s article.
Three Questions You Need to Ask About Your Technology

Technology is an essential component for most businesses. Strategic integration of technology has been proven to address significant operational challenges that often elude smaller businesses and startups. In this context, we’ll explore three critical questions about business technology that every tech-savvy individual should be acquainted with and make clear the importance of such knowledge.
Why Outsourcing Your IT Management Has Huge Value

Cost/Benefit is a term you hear a lot. It’s always used in conversations about potential investment and means something. Well, at least it should. One of the places that many people can gain benefits from their investments is by outsourcing some of their responsibilities to an outside vendor. This works especially well with IT management. […]
How Digital Signs Can Transform a Business’ Message

Research suggests that digital signage outperforms other forms of media in effectively capturing the attention of viewers. It also offers the flexibility to present diverse types of content within confined spaces. This results in enhanced engagement and an overall visibility of messages.
