What We Can All Learn From the VirusTotal Data Leak

In 2004, a service called VirusTotal was launched and swiftly became a popular antivirus and malware scanner to help detect threats in various files and URLs. It became popular enough that it was officially acquired by Google in 2012 and ultimately assimilated into Chronicle, a cloud-based security operations suite for enterprise businesses. Despite this impressive […]
Dissecting the Lessons from a Recent Amazon Scam Warning Email

Amazon Prime subscribers recently received an email from the online marketplace, warning them of the prevalence of scams that took advantage of their offerings and brand recognition. Let’s go through the advice that this email shared, and compare it to the best practices we recommend for avoiding scams.
Do You Know How Much You Should Be Spending on Cybersecurity?

Nowadays, you can’t afford not to have some portion of your business’ budget set aside for cybersecurity. The question is, how much do you need, and what should you be spending it on first? Let’s take a few moments to dig a little deeper into this question and examine a few cybersecurity protections you should […]
Blank Emails are a Sign of Dangerous Spam

We talk a lot about phishing. What it is, what it does, and perhaps most critically, what it looks like. However, have you ever expected a phishing email to look like… nothing? As in, a completely blank message? If you answered, “no,” that’s exactly what today’s cybercriminals are counting on.
What is It About the IoT that Makes It an Appealing Target for Cybercrime?

The IoT—the Internet of Things—is a fascinating technology, as it exemplifies just how much can be accomplished when Internet connectivity is used to augment the capabilities of otherwise “dumb” devices. Unfortunately, as fascinating as it is, the IoT is also infamous for its security issues…a reputation that attackers have been perpetuating as these devices grow […]
What are (Probably) Your Biggest Cybersecurity Threats?

Of all the cybersecurity threats out there for your business to contend with, there are going to be a few of them that are just more likely to impact you than others. That’s just a statistical reality. Fortunately, these threats can be addressed, so let’s discuss how you can do so.
Which Security Issues Should You Watch Out for In Your Business?

While it is important that your business implement comprehensive network protections, there are plenty of simple ways that your business’ cybersecurity could potentially fail. This could easily cost you heavily in your available capital, financial and social alike.
Can AI Be Trusted to Stop Phishing?

AI—artificial intelligence—has been a hot topic as of late, with it seemingly being used for any purpose you can imagine nowadays. Unfortunately, this has also included cybercrime. However, just as AI can be a weapon for cybercriminals to use, it can also be a shield to help protect your business from threats. For instance, in […]
If You Think a Consumer-Grade VPN is Worth It, Think Again
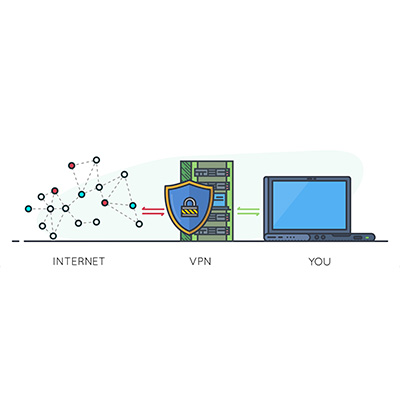
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses use a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Let’s go over why a VPN is so effective, as well as […]
Incorporating Insights From Enterprise Companies Can Benefit Your Business’ Security

Businesses cannot afford to grow complacent with their network security, as it could make a significant difference between falling prey to an attack and remaining secure. The process of securing a network must be looked at holistically, from top to bottom. This idea of enterprise security is not new, but even a small business needs […]
